When scrappy little startups succeed in putting a dent in multi-billion dollar businesses, entrenched corporations that are under attack tend to get very nervous. Not everybody embraces change.
Inevitably, some of them will resort to shady tactics to hinder, counter or completely stop challengers from posing a threat to their core business.
This morning, a Hacker News thread led me to this blog post, in which Hamburg, Germany-based Michael Büker exposes a nasty trick and smear campaign from 1&1 Mail & Media, a subsidiary of United Internet, one of the world's largest web hosting and webmail companies.
Hiding their identity as good as they legally can, United Internet - which operates free webmail solutions Web.de and GMX.net through subsidiaries - is apparently trying to trick millions of users into uninstalling certain Google Chrome and Mozilla Firefox extensions, the most famous of which are Adblock Plus browser add-ons.
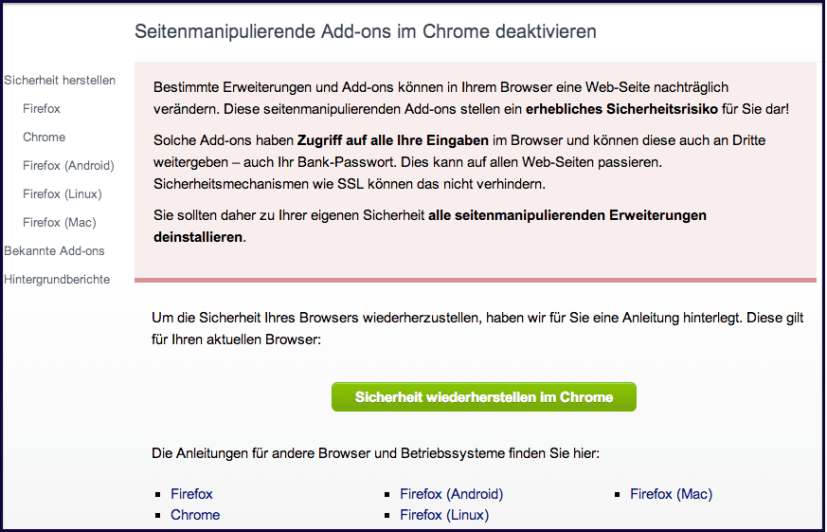
It does so by leading users of its GMX and Web.de webmail products to a website browsersicherheit.info ('browser security' dot info) via a yellow website bar, misleading them into believing they're visiting an innocent site that lets them configure their browser settings.
The site is designed to look like a security settings page, and only a small greyed-out 'Imprint' text at the bottom of the page shows the identity of the website publisher (you guessed it, 1&1 Mail & Media).
The browsersicherheit.info website goes to great lengths to instil fear in users' minds, tricking them into thinking their security is at risk for using browser add-ons that are merely designed to block advertisements (which is of course United Internet's main income from free webmail products).
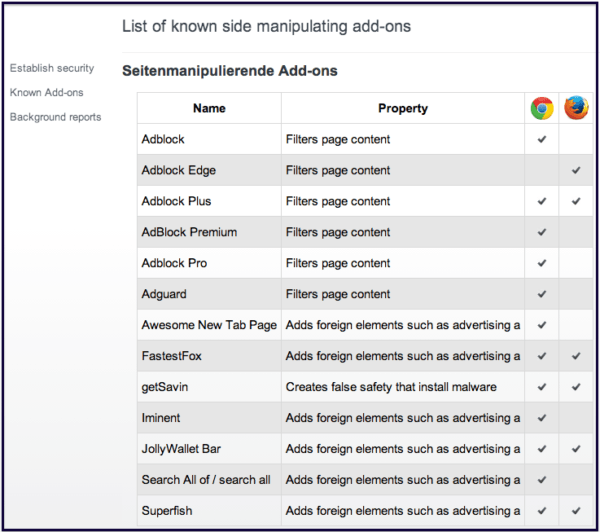
Users are invited to learn how to 'restore security' by disabling and removing the supposedly unsafe browser extensions, singling out Adblock Plus products for 'filtering page content' (cute, United Internet), Adguard, Awesome New tab Page and a handful of others.
From the looks of it, though, Mozilla is aware of the issue and is apparently already looking into it.
There's also some movement over at Adblock Plus, apparently.
@emtiu Perhaps it’s time for a new extension: BullshitBlock. (How much web would be left, though?)
— Jesse Ruderman (@jruderman) February 26, 2014
Bullshit indeed.
This FUD campaign is a brazenly sneaky way of protecting one's business, and United Internet should be deeply ashamed for trying to mislead its users and making them believe their security is compromised by browser add-ons that aren't developed and distributed with malicious intent at all.
These companies should be looking at ways to evolve with the times and ask themselves why dozens of millions of people install ad-blockers in the first place, instead of trying to protect their established business in such shady ways.
There's also talk of certain German media and online marketing companies looking into ways to sue Adblock Plus parent company Eyeo, which is based in Cologne.
For shame.
I've contacted United Internet (which also owns Mail.com and Sedo) and 1&1 to learn what compelled them to sink this low, as well as Eyeo CEO Till Faida but haven't received any responses so far.
Update: Web.de spokesman Thomas Plünnecke says:
We see the warning as a contribution towards more security on the Internet, because especially software on users’ devices can be a gate for attackers. Not all users are aware of the kind of add-ons they have installed and of the risks in changing a website’s content.
There are examples for add-ons being used to pass out content from the US. What scared us was, how easy it is to manipulate add-ons; and especially that they were not found by virus scanners in a lab test, which was confirmed by manufacturers of anti-virus software. The result: with just a few lines of code, an add-on can turn into spyware.
More on that here: http://www.computerbild.de/artikel/cb-Aktuell-Sicherheit-Bad-ons-kapern-Rechner-9767605.html
This was our reasons (sic) to warn our users and make them aware of the installation in their browsers.
When asked why they resorted to trying to hide their identity, Plünnecke said:
It may be true that the sender of the message was missing at first. We have revised the info box and it now clearly mentions WEB.DE and GMX as senders of the warning message.
The website www.browsersicherheit.info however has deliberately been chosen to be neutral because it is a comprehensive action, which other partners can link to. A browser, aside from transmission paths and data storage location, is the most important element of Internet security.
As a provider, we take care of secure transmission and storage locations, but we need a user’s help to ensure the security of the browsers on their devices.
Update 2: a statement from a Mozilla spokesperson on the topic:
"We are aware of websites showing deceptive messages that attempt to persuade people to uninstall certain Mozilla Firefox and Google Chrome extensions.
At Mozilla we have a blocking mechanism to protect users from malicious add-ons, and often post relevant security alerts to our security blog: https://blog.mozilla.org/security/
Always be wary of scams or suspicious messages prompting you to install, upgrade or uninstall software from an unknown site."
Featured image credit: igor.stevanovic / Shutterstock