(Editor's note: This is a four-post series on Bitcoin. This second post will attempt to shed light on the Bitcoin ecosystem and how the crypto-currency is powering new kinds of businesses. For more information on the basics of Bitcoin, check the first post of the series).
In the previous post about Bitcoin, we discussed the actual protocol and how it works. Building on that, we'll extend some notions of the protocol and will take a deep dive into the actual Bitcoin ecosystem.
The Bitcoin Network
Bitcoin runs its own distributed, peer-to-peer, network of nodes. This network is composed of clients that generate transactions, nodes that validate transactions, and miners.
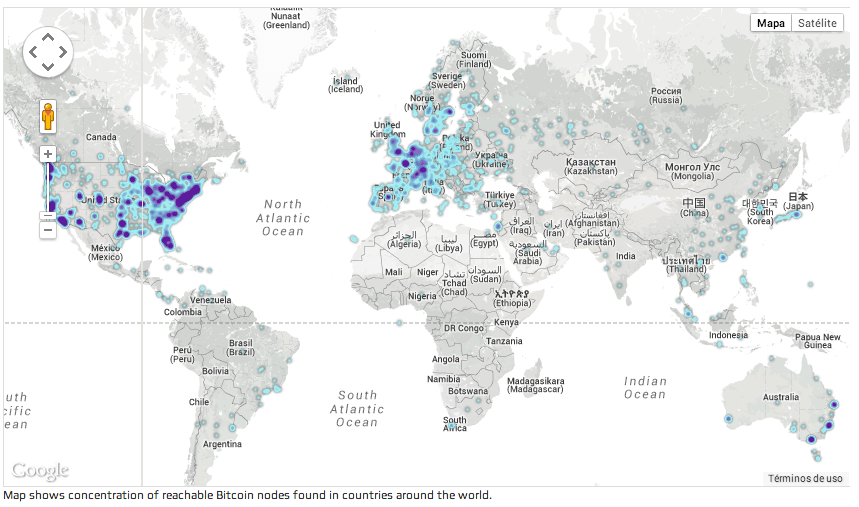
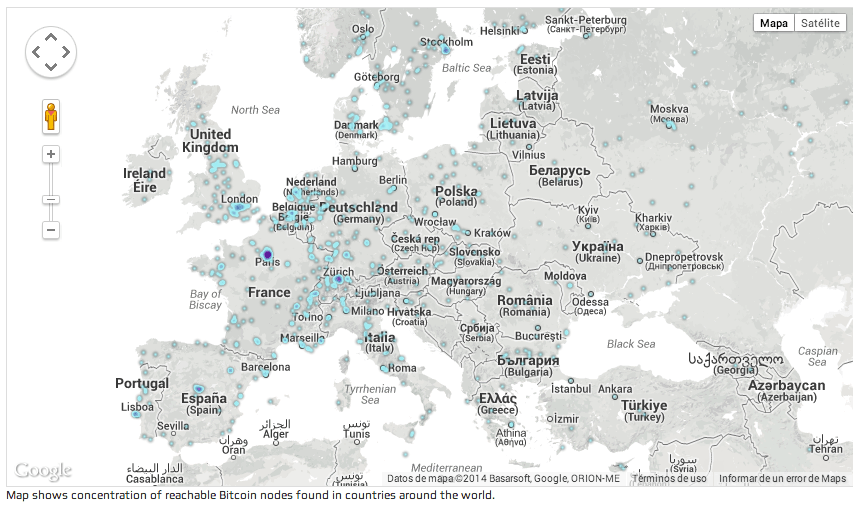
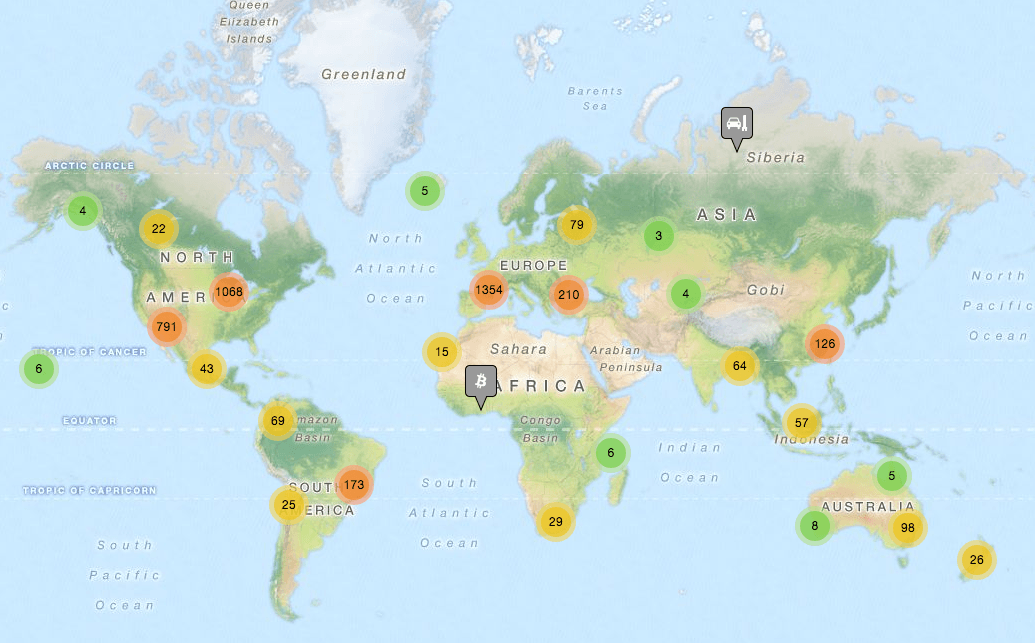
Fig. 1: Bitcoin network geographic node density (Worldwide & Europe details)
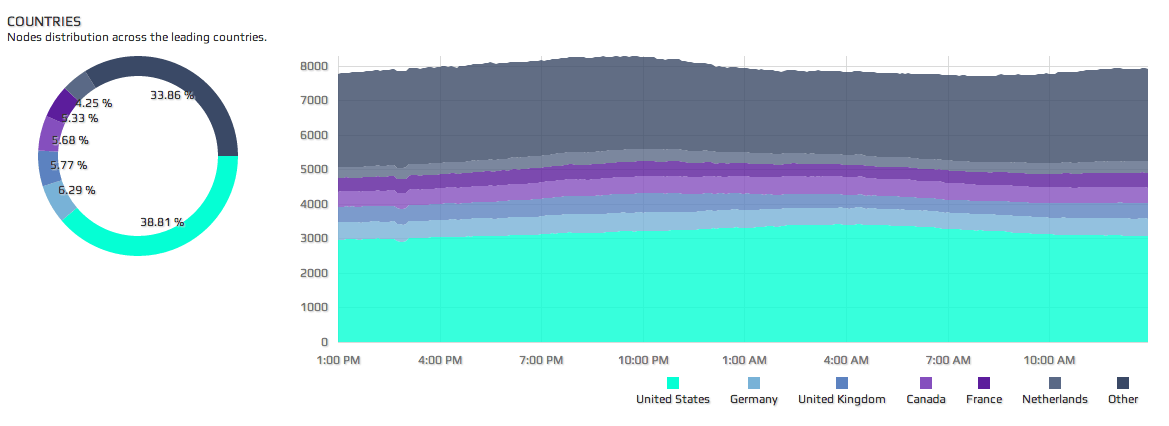
The following maps from Bitnodes, show the localization and extension of the Bitcoin network. While the US is the number one country in terms of volume (38.81%), if we combine the top European countries, it accounts for around 25% of the network, way beyond China's 4%.
Fig. 2: Fluctuation of country distribution of the Bitcoin network
Fig. 3: 24 hour fluctuation of nodes of the Bitcoin network
While the country fluctuation of the network is more or less stable, the node fluctuation is more severe, peaking at 8300 nodes, at around 9 pm GMT +2 (CET), which is afternoon in the US (4pm EST, 6pm PST). This is interesting because it shows that around 7.22% of the Bitcoin network is composed of clients that are run periodically - rather than steady nodes.
Apart from the network infrastructure distribution, it's becoming increasingly important to determine the location and the cataloging of brick and mortar vendors, providers and services that accept Bitcoins. Coinmap is one of the first approximations to a 'Google for Bitcoin' service.
Fig. 4: Map of physical vendors accepting Bitcoins
Getting Bitcoins
The first thing asked by anyone who takes up an interest in Bitcoin is: how can I get Bitcoins? There are several ways to obtain them. Essentially you can buy Bitcoins through a currency exchange site, you can mine Bitcoins and earn some in return, or you can get them from someone who already owns Bitcoins.
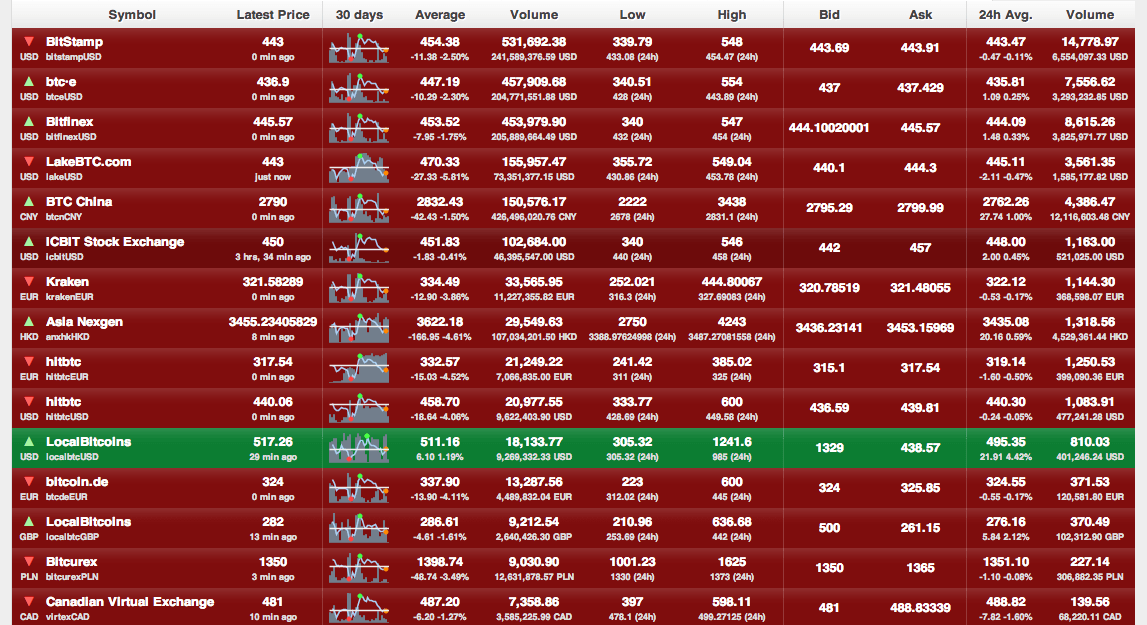
The Digital Currency Exchanges (DEC) were one of the first structures to appear in the Bitcoin ecosystem. Names like Bistamp (Slovenia), BTC-e (Bulgaria), BTCChina or Bitcoin.de (Germany) are some of them. The big absentee is Mt. Gox, a Digital Currency Exchange that recently went bust.
Fig. 5: List of the top 15 Bitcoin Currency Exchange markets (Source: Bitcoincharts)
When it comes to trading though, it seems the US dollar is the preferred currency, followed by the Chinese Yuan (CNY) and then the Euro (EUR), so despite the lack of infrastructure, there are, so far, more Bitcoin transactions happening in China than in Europe.
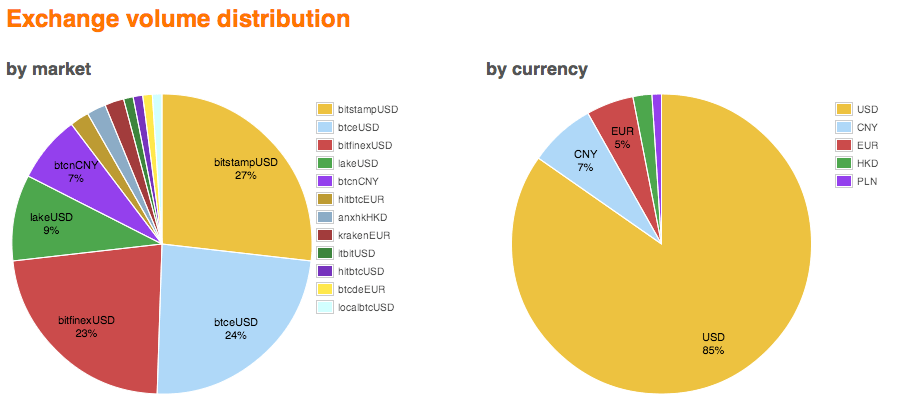
Fig. 6: Bitcoin Currency Exchange market volume (Source: Bitcoincharts)
The Mt. Gox incident
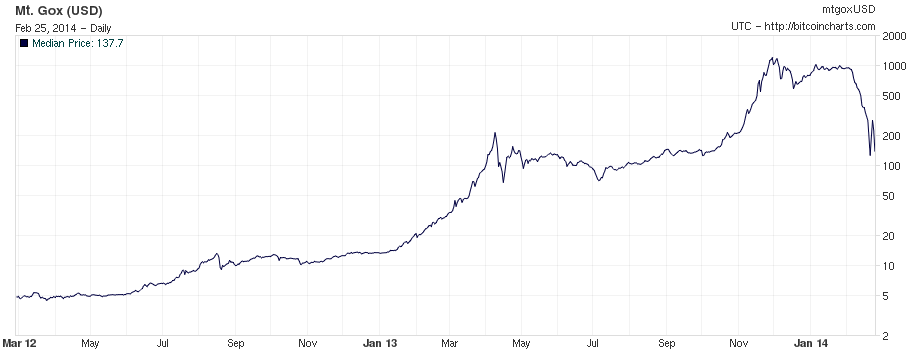
A lot of what people know about Bitcoin is because of the Mt. Gox scandal. The currency exchange was a company based in Tokyo, Japan, founded in July of 2010 and run by Mark Karpelès since March 2011. In 2013 it held a near monopoly, commanding close to 80% - 90% of the US dollar-denominated volume.
On February of 2014, Mt. Gox stopped trading altogether, after months riddled with problems. Since mid-2013, Mt. Gox's customers had been unable to withdraw funds without problems, with average delays of around one month.
Fig. 7: Mt. Gox Bitcoin Exchange volume from February 2012 - February 2014
By the end of February of 2014, Mt. Gox admitted to have lost around 750.000 Bitcoins, roughly around 470 million dollars at the time, blaming it on flaws of the Bitcoin protocol.
The incident generated major news headlines around the globe and has, sadly, been used to taint Bitcoin as unsafe and extremely volatile, prompting some governments to ban it altogether.
Truth is, Mt. Gox amassed a ridiculous amount of security flaws since 2011, when their user database got robbed and leaked, exposing a lack of security engineering knowledge. As the currency exchange rose in popularity and the Bitcoin price increased, it steadily became the target of more sophisticated attacks. These led to the inevitable collapse of the exchange due to poor management decisions.
Transaction Malleability
Among the many issues that Mt. Gox experienced, attacks based on transaction malleability have been blamed for the loss of many of the Bitcoins. A study by two researchers from the ETH Zurich University proves that, while there's been around 302.000 Bitcoins under attack worldwide, only 386 Bitcoins had been effectively stolen from Mt.Gox.
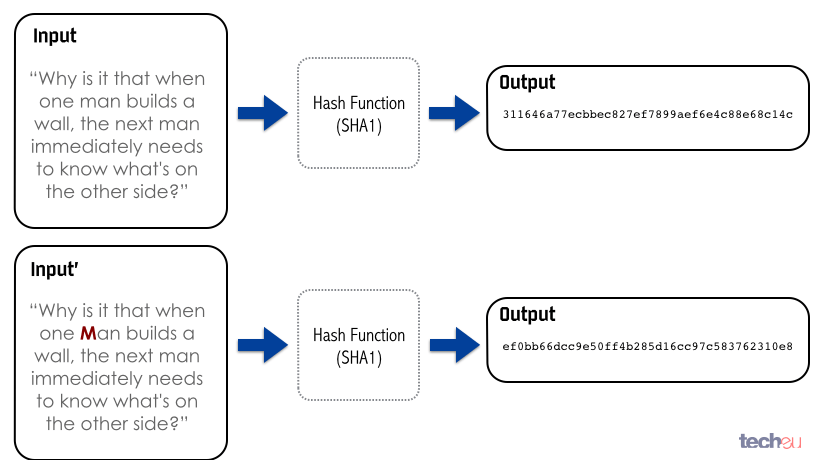
The incident has, however, brought a well-documented Bitcoin issue to the spotlight: transaction malleability. This happens when two identical transactions generate two different transaction IDs or hashes.
Fig. 8: Example diagram of a hash function
A hash is the output of a crypto-graphic function that generates a fixed-length alphanumeric representation, the hash, of the data it receives as an input.
There are two major key aspects to a hash. It needs to be a unique representation of the data, that is, you can't have two different sets of data that will generate the same hash. Any modification to the original data, even just a bit, should generate a different hash. The other aspect is that a hash can't be reversed, you can't obtain the original data the hash was calculated from.
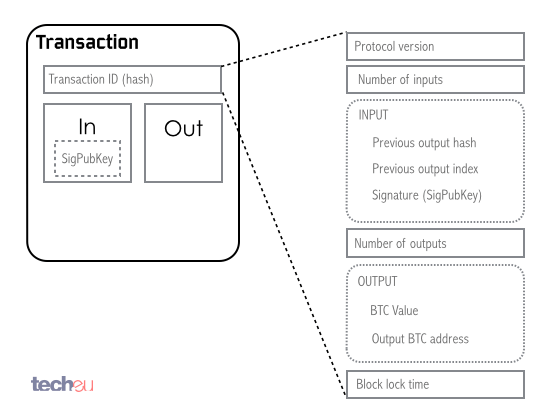
Bitcoin employs hashing extensibly, and all transactions have their own hash for integrity reasons. The hash is calculated by concatenating all the fields from the transaction, so in theory, you could consider the transaction hash a unique ID.
Fig. 9: Bitcoin transaction hash composition
That uniqueness isn't real, however. Two transactions can exist with the same inputs and outputs, valid signatures but with different hashes. This is what is called, transaction malleability, and as you would suspect, it's quite non-intuitive.
On the previous post we described how each transaction is signed by the sender with their private key. What isn't well known is that the Bitcoin protocol doesn't use all of the transaction fields for the signature. The process is quite complicated but what's important to understand that there is a small fragment of the transaction (ScriptSig), that can be changed without invalidating the cryptographic signature, although it will generate a new hash.
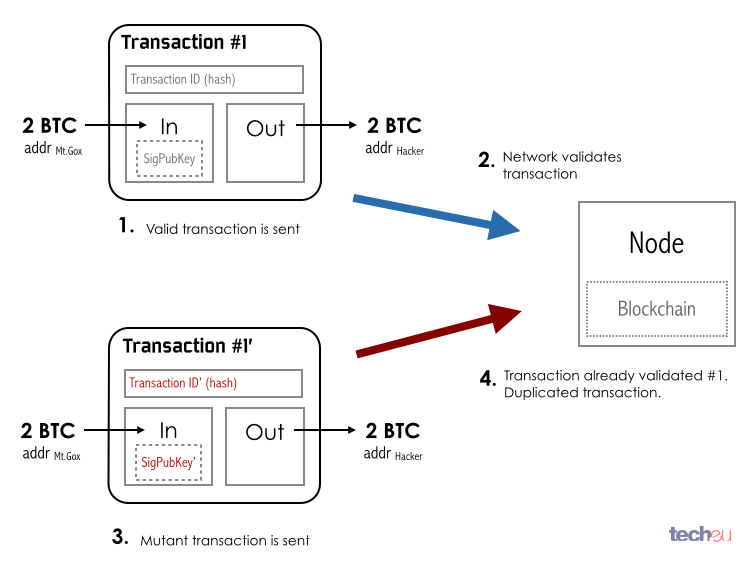
All this means that a malicious party can create two transactions that are both valid, cryptographically speaking, but with different hashes as identifiers. One of them will be valid, the other is called a mutant transaction and should be discarded.
Fig. 10: Bitcoin mutant transaction regular behavior
Mt. Gox had a bug in their processing software that identified both transactions as different. According to the regular working of the protocol (Fig. 10), the mutant transaction is discarded but the valid one will be accepted.
In the case of Mt. Gox, the mutant transaction that failed was handed to their software, which incorrectly identifies them as two different transactions (Fig. 11), and proceeded to resend the payment, effectively paying the attacker twice.
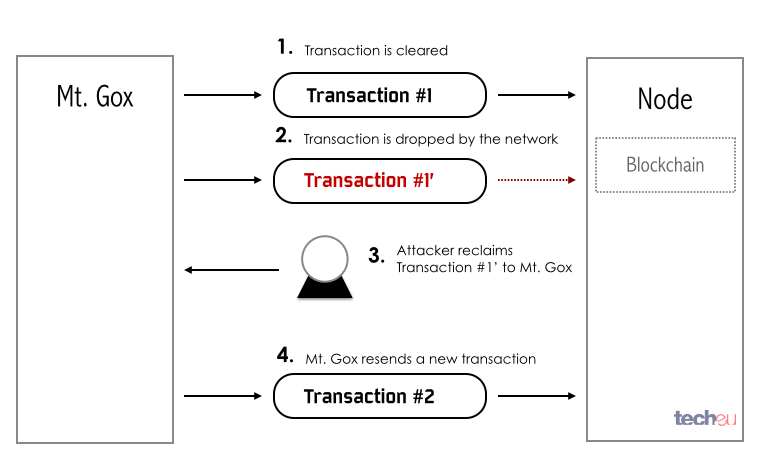
Fig. 11: Mt. Gox mutant transaction bug
Bitcoin wallet types
The next step in the Bitcoin evolution was the creation of software that allowed the sending and receiving of Bitcoins, or as we saw on the previous post, transactions. This piece of software is called a Bitcoin wallet.
Initially there was only one type of wallet, the Bitcoin-Qt client. This software, which runs as a desktop application, is both wallet and Bitcoin network node. It connects to the Bitcoin peer-to-peer network, downloads the blockchain and serves as a validating agent capable of mining if necessary. These type of clients are called 'full clients'. The drawback of such wallets is that the user needs to download the whole blockchain, which is around 20GB and growing, plus run a Bitcoin node.
As the Bitcoin ecosystem started maturing, new wallets came into existence that only did one thing, handle the user's Bitcoins. These clients are called thin clients, as they don't need the entire blockchain but only the last fragment - and they don't run nothing more than the logic needed to send or receive transactions. Interestingly enough, two of the most important ones, Hive (Krakow) and MultiBit (London) are actually developed in Europe.
Thin clients, while faster and lighter than the full client counterparts, are less secure. The fact that they don't contain the whole blockchain makes them vulnerable to specific attacks.
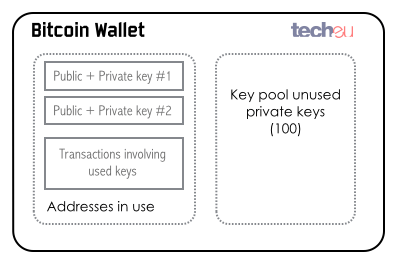
The wallet software essentially holds the list of public-private cryptographic keys, the derived Bitcoin addresses and the list of transactions done with those keys.
All these pieces of information are stored on a file, usually called wallet.dat, but it depends on the wallet client vendor. This file is critical for the retrieval and usage of any Bitcoins owned in the wallet, as it holds the private keys that will unlock them. If the file is damaged, stolen or lost, the Bitcoins held in that wallet will be lost forever.
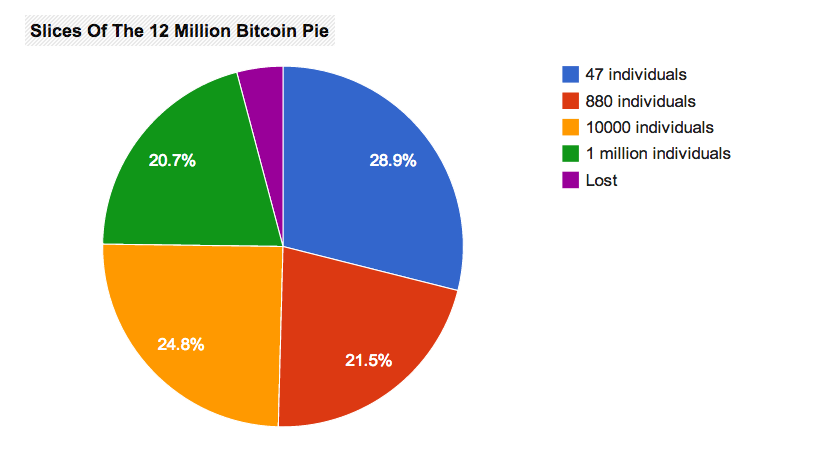
Fig. 12: Bitcoin ownership circa December 2013 ~12 million Bitcoins in circulation (Source: Business Insider)
As more (relatively) early adopters enter the Bitcoin arena, wallet software is becoming increasingly critical. Ease of use, security and backup capabilities are among the chief requirements.
Wallets started originally as desktop software but with the increase in interest, there is a whole crop of websites that offer online wallets or even mobile wallets (more on this on the next post of the series).
While online wallets are more versatile than their desktop counterparts, there is a big security tradeoff. Online wallets users rely on the company's resources to keep their private keys protected. On the other hand, desktop wallet users will need to enforce their own security themselves.
Fig. 13: Bitcoin wallet mechanism
Blockchain forks
But why is the blockchain so important for Bitcoin and its wallets? As we saw before, the Bitcoin network has no central authority that validates a transaction. Transactions are validated by the network itself, in a distributed fashion.
The problem with this distributed mechanism is that, there is a small window of time where two identical transactions might coexist, potentially creating a double spending situation, until all the nodes of the network agree on a specific blockchain order.
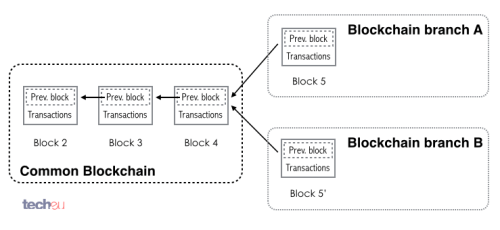
One of the problems with such a distributed network is how to keep this order. It could happen that two different miners generated different blocks at the same time in a way that the network wouldn't have enough time to propagate the current status of the Blockchain, generating two different copies of the chain. This is called a fork in the chain.
Fig. 14: Bitcoin Blockchain fork
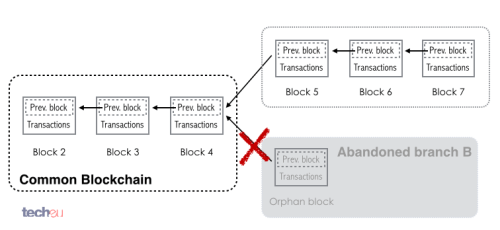
At this point, each node will keep both branches alive, having miners working on both. The miners though, keep track of which branch is getting ahead, that is, which worked faster. The moment one of them gets ahead, miners working on the shorter one will get prompted to cease any work and switch to the longer branch, eventually condemning the shorter one. The blocks pertaining to the abandoned branch are called 'orphan blocks'.
Fig. 15: Bitcoin Blockchain branch merging
Transaction confirmations
When a node accepts a transaction as valid, it will add it to the block and broadcast the new block to the rest of the network. This process is known as confirmation. As new transactions come in, new blocks will get added after the one that contains the validated transaction.
Each time a new block is added to the blockchain after this one, the confirmation count grows. The more confirmations, the more legit the transaction is.
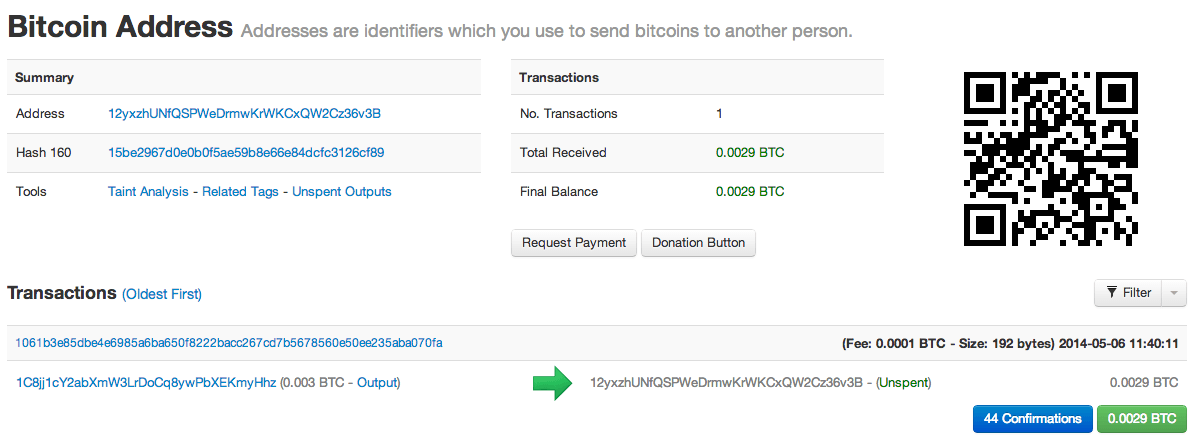
Fig. 16: Example transaction with 44 confirmations
The reason is that, as seen before, the blockchain might have a fork (Fig. 14). If we accept a transaction before waiting for at least six confirmations, it might happen that the network drops that branch, effectively rendering the transaction void, exposing us to a fraud situation or double spending.
Fig. 17: Bitcoin transaction confirmation process
Why six confirmations? Because generating an alternate Blockchain branch bigger and faster than the rest of the network would require vast amounts of computational power. Even if an attacker owns 50% of the computational power, it would have a 1% chance of subverting the legitimate blockchain, thus minimizing any double spending attempts.
Mining pools
We also talked about a second way of earning Bitcoins through mining. Mining is the process by which the Bitcoin network validates transactions, through the calculation of what's called a Proof of Work (PoW).
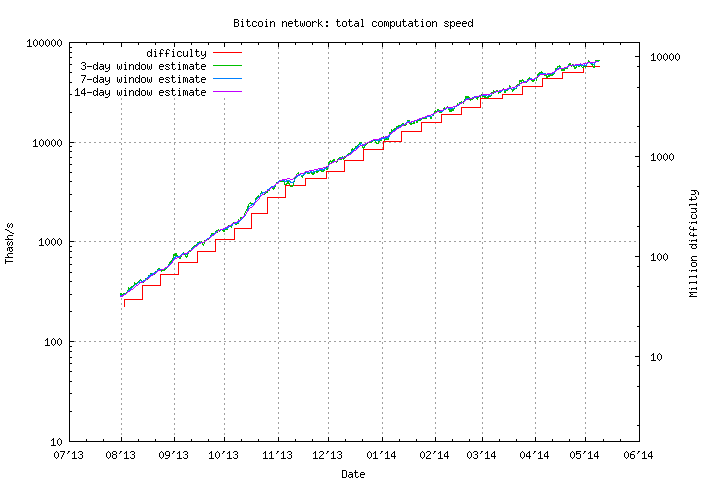
The problem with mining is that, as more people get into it, the network self-regulates the difficulty of calculating the Proof of Work.
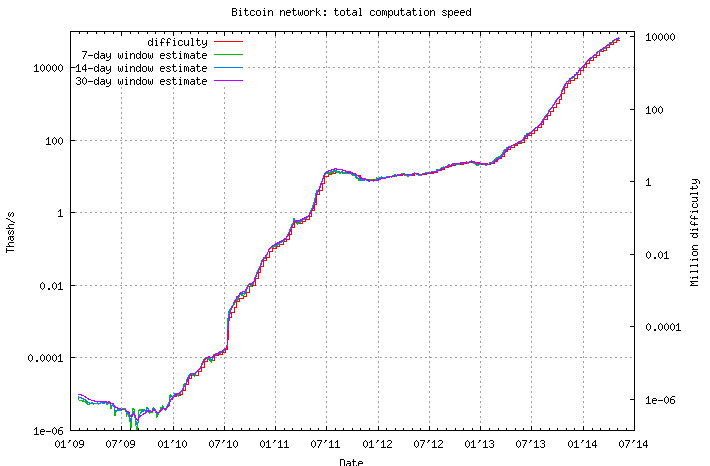
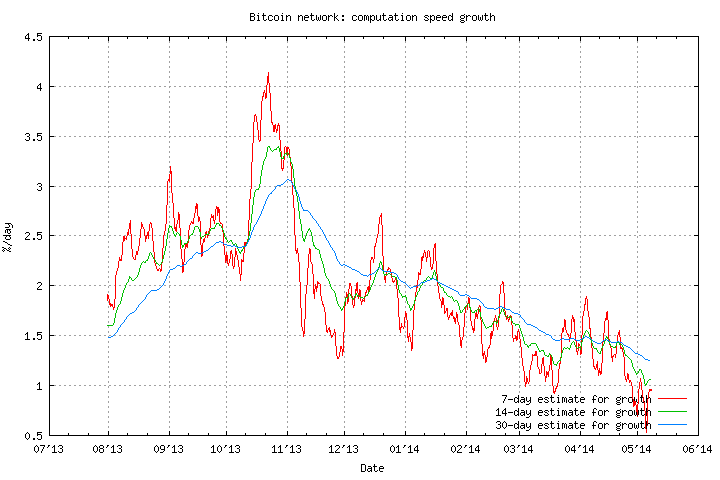
Fig. 18: Total computation and difficulty growth of the Bitcoin network
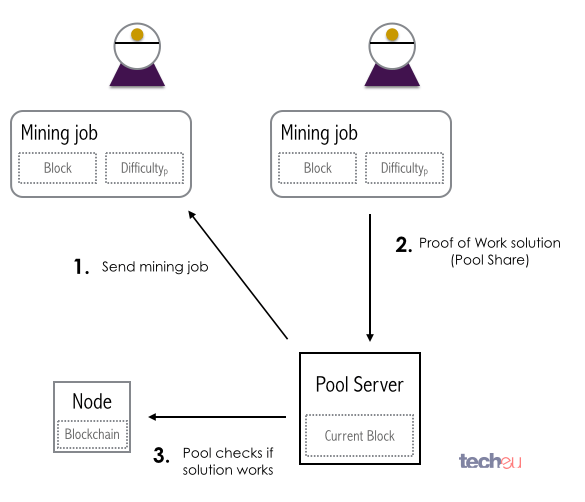
The harder the mining becomes, the more computational power is needed to generate new Bitcoins. What people figured out early on is that, instead of mining themselves, they could band together, break down the Proof of Work into smaller fragments and have each party calculate a subset of the problem.
Fig. 19: Example of how a mining pool works
The partial solutions found by each miner in the pool, called mining shares, would then be received by the pool server and tested as valid Proof of Work with the Bitcoin network. This is called a mining pool.
Any successfully-mined block will generate new Bitcoins for the miners, a transaction called Coinbase. In the case of a mining pool, the newly generated Bitcoins will be split among the members of the pool according to their contributed processing power or mining shares.
As you can expect, there are many different mining pools with different schemes of rewards ranging from Pay-per-Share (PPS), Scoring or Capped Pay Per Share with Recent Backpay (CPPSRB). Each of these mining pools have their own rules, rewards and memberships. Some of them anyone can join, others are private. Even though now it has a smaller share, the first mining pool that ever existed was Slush, out of the Czech Republic.
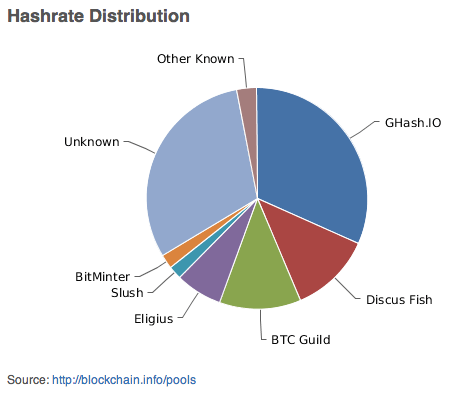
Fig. 20: Bitcoin mining pools hashrate distribution
From a software perspective, there are two critical pieces to mining, the software that does the actual calculations of the Proof of Work, and the protocol that connects each miner with the mining pool. The first one is called mining software and might be capable of supporting one or more mining protocols like Stratum, Getblocktemplate or the legacy GetWork.
Fig. 21: Bitcoin mining farms (Source: Bitcoinexaminer)
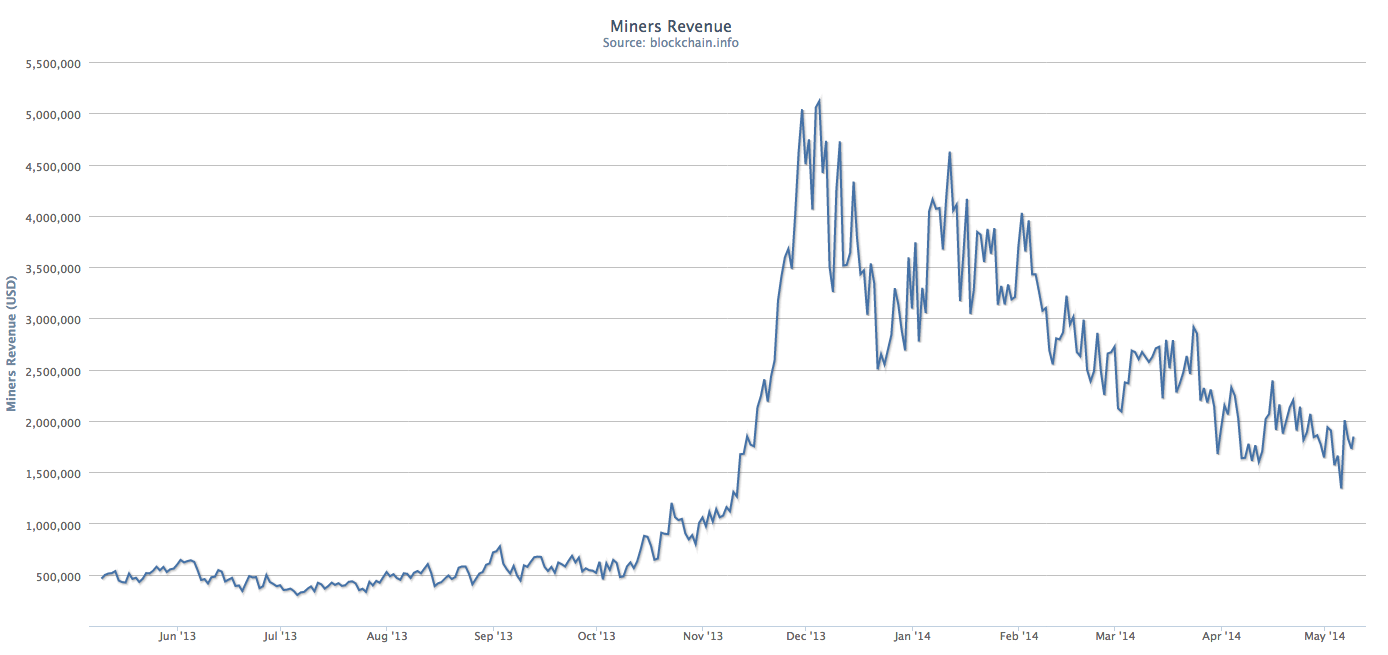
While mining is computationally expensive, as the price of Bitcoins went up, it became a very lucrative business. So lucrative, that people started deploying specialized hardware to mine Bitcoins. Right now there are even specialized companies selling Bitcoin mining gear ready to use.
The mining race is so intense that some have questioned how environmentally friendly it is. The fact is, the incentive to lower consumption rates of mining hardware is more an economical one, than an environmental one.
Fig. 22: Bitcoin computation growth and size (Source: http://bitcoin.sipa.be)
All this said, it seems the mining frenzy is slowing down. Computational growth, that is, the number of new machines mining Bitcoins, has dropped drastically during this year, decreasing below the 1% growth mark from an impressive 4% back in October of 2013 (Fig. 22).
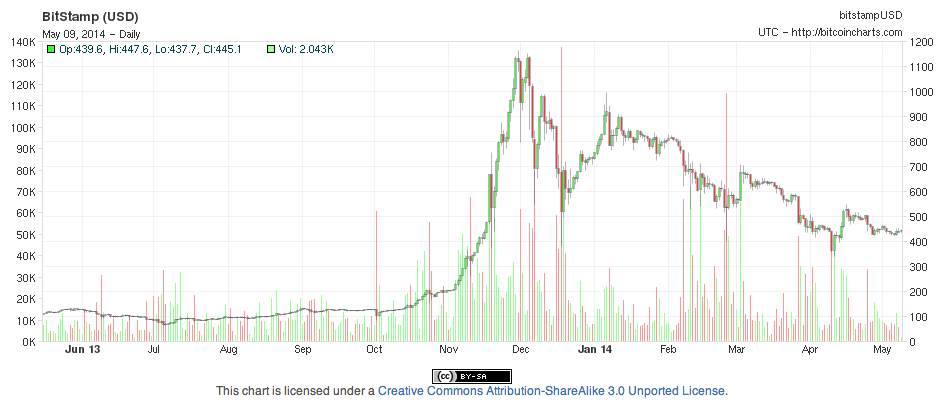
The explanation is quite simple: the value of Bitcoin has been steadily declining from an all-time high in December of 2013, while, for example, electricity costs in the US have been increasing by an average of 5.7% across all sectors.
Fig. 23: Bitcoin - USD one year evolution (Source: Bitcoincharts)
Be sure to check back for more
As always, it's impossible to cover all the interesting things going on with Bitcoin, so stay tuned for our next post in the series. It will be devoted to Bitcoin wallets, security aspects like anonymity and Bitcoin contracts. In true Bitcoin fashion, you can also donate Bitcoins if you're liking the series: 13kbYPnPbhPALfCpSeMgairFYj3W7etRTx.
Featured image credit: Arina P Habich / Shutterstock






Would you like to write the first comment?
Login to post comments