(Editor's note: This is the third post in our four-part Bitcoin series. Here, we take try to uncover the world of Bitcoin wallets: types, security and new trends. In case you missed it, our first post covered the basics of Bitcoin and the second one looked at the Bitcoin ecosystem).
In the previous post, we gave an overview of what the Bitcoin ecosystem looks like – it's an ever-expanding ecosystem, one where wallets play a special role as they're one of the major driving forces of the Bitcoin industry after trading and payment gateways.
Bitcoin wallet threads
The rise of Bitcoin prices are indeed turning wallets into a target for all kinds of cyber attacks. A 2013 report on Financial Cyber threads by security company Kaspersky shows how aggressive cyber criminals are taking to Bitcoin.
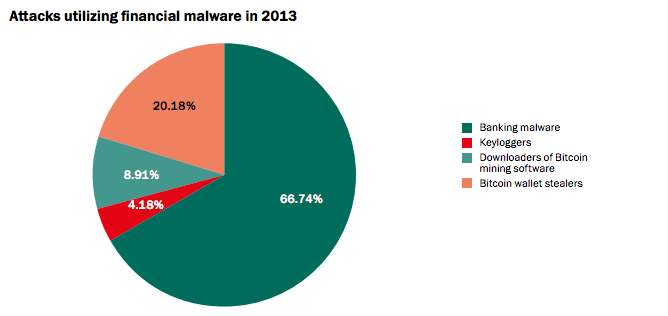


Figure 1: Growth of cyber threads on Bitcoin in 2013 (Source: Kaspersky Labs)
The variety of attacks are also widening considerably. According to Dell's SecureWorks Counter thread unit, the amount of malware families targeting cryptocurrencies has surpassed 100.

Figure 2: Correlation between Bitcoin price, new malware emergence and total threat of cryptocurrency-stealing malware. (Source: Dell SecureWorks)

Figure 3: Top Cryptocurrency Stealing malware families and their detection rate across AV vendors. Feb, 2014. (Source: Dell SecureWorks)
As always, attacks supersede the speed at which wallet vendors are capable of developing new secure features. The Bitcoin security space is definitely one of the growing niches of the cryptocurrency. It's not only wallets under attack, but any trading system that stores Bitcoins. In April, Finnish trading platform Localbitcoins was under attack and, once again, about a month ago.
The truth is, at this point, most Bitcoin startups (including wallets) are developed by volunteers – no money is being earned from them and security is expensive. As long as there's no business model behind Bitcoin wallets, it will continue to be difficult to get funding for them, although that might be about to change.
Bitcoin wallet clients
Surprisingly, while Bitcoin acceptance in the media and in broader circles is growing rapidly, the pace of Bitcoin startup adoption isn't exactly keeping up. The lack of a selection of Bitcoin wallet software is shocking. Although there are several new wallets coming out every couple of months, most remain relatively unknown or lack important functionality.
The following is a list – by no means complete – of the major Bitcoin wallets in existence. We played with some of them to get a feeling of how they worked. Each of them have their pros and cons, but only with time (and funding) will the winner reveal itself.
Desktop wallets
Hive (thin client): It's probably the slickest of all the wallets we tried. Great interface and user experience but they might have sacrificed too much functionality, especially security mechanisms, for the sake of usability. Hive is developed by European developers, mainly from Krakow.

MultiBit (thin client): Nice thin wallet client based out of London. It allows more control than Hive but has a rather basic user interface. So far, it doesn't support the euro currency, but most importantly, any new wallet created with MultiBit comes unencrypted by default. Some basic usability improvements are needed on MultiBit. Despite this, it's currently the top wallet by installations worldwide.

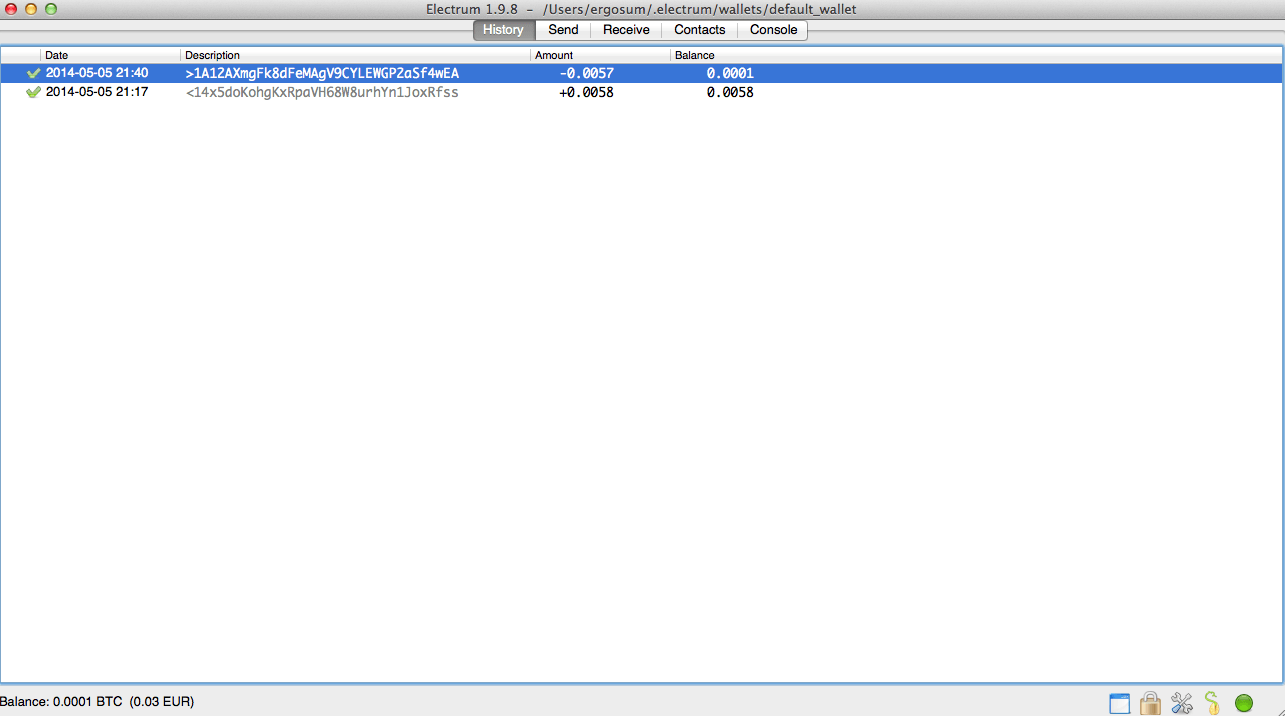
Electrum (thin client): It's a very bare-bone client out of Germany and Amsterstam. It's hard to use with such a minimal user interface and there's really no user experience to talk about. Although I have to say, despite its looks, Electrum is one of the few to implement advance wallet capabilities. My guess is, the moment they hire a good designer, the wallet will improve drastically.
Bitcoin-Qt (full client): This is the original Bitcoin client and has a slicker interface than the previous two but still quite spartan on what you can do with it. The feeling is that this client has been used as template for all the other ones. Hopefully though, wallets such as Hive are showing that you can design a wallet differently. The major problem with this client is that it requires downloading the whole Blockchain, that is, 20GB of data. It also doesn't encrypt the wallet by default, which poses a security risk.

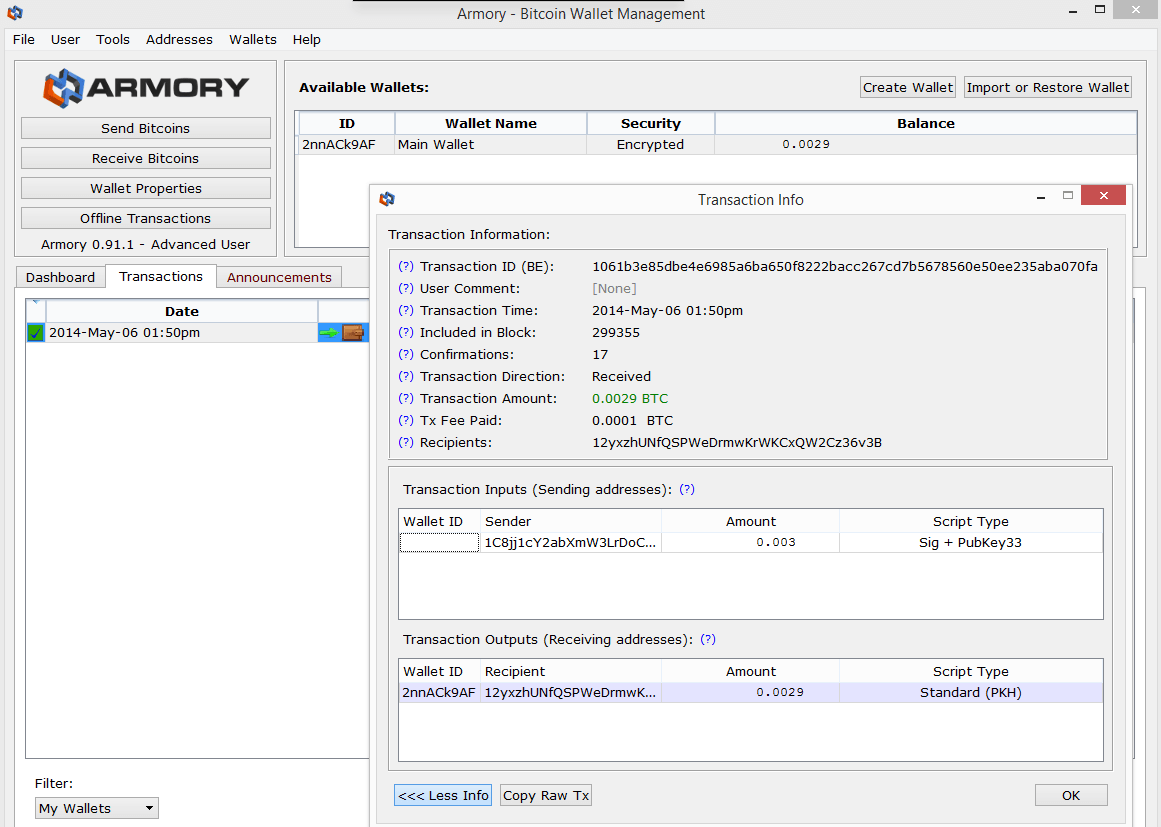
Armory (full client): Definitely my favourite of the bunch by far. It's raised $600,000 in seed funding and is clearly putting it to good use. Designed with security-by-default in mind, it strikes a nice balance between usability and security. Armory was also one of the the first to innovate on the wallet side by implementing things such as watch-only wallets. The major drawback, again, is that it relies on the Bitcoin-Qt client to work, which means going through the hassle of downloading the Blockchain.
Online wallets
After the initial Bitcoin client was released, people started to realize that for Bitcoin to spread, you couldn't rely on desktop wallet adoption. While desktop wallets are more secure, it requires very technical early adopters. Larger adoption requires easier solutions and that's what online wallets provide. They offer users ease-of-use by – for the most part – taking care of security for them, but can also expose them to major security breaches like that of Paytunia.
As you can imagine, there are plenty of online wallets, some of them more advanced than others, of course. To name a few in this category, there are options such as Coinbase, BitGo, GreenAddress and Xapo or simpler ones such as EasyWallet or Kipochi.
Hybrid online wallets
These wallets are a blend between online and desktop wallets. It's a step up in security from standard online wallets. Essentially, these wallets encrypt private keys in the user's browser and then send them to the online site for storage. This way, even if the online wallet is breached, the attackers still need the user's password to decrypt the wallet's keys. Some examples are Strongcoin, Blockchain or Carbon Wallet.
These new types of wallets are definitely growing in popularity – to the point that they're being integrated as browser plugins like KryptoKit or its competition, the Dark Wallet, which is already in alpha testing.
Mobile wallets
Of course, this list wouldn't be complete without the mobile counterparts. Some mobile wallets are basically another version of previously-mentioned wallets, like Blockchain or Coinbase.
The following are purely mobile:
Bitcoin Wallet (thin client): A very neat application covering the basics. I exported the address through the QR code into Hive and it worked like a charm. You can't do advanced operations but for the basic payment operations, it's more than enough. It also allows the user to backup the wallet and send it anywhere you want for storage.

Mycelium (thin client): This is another option that is very simple, although I found it harder to use than Bitcoin Wallet. Mycelium could use some user interface love, but it works – which is the important thing. It's the evolution of Bitcoin Spinner, also from Danish developer Jan Moller.

Bitcoin wallet security
Wallet protection has become a very important issue in the Bitcoin industry. In this realm, wallet theft protection is a chief issue – anyone that has access to your wallet file is, effectively, in possession of your Bitcoins. One of the obvious steps to prevent this, is to encrypt the wallet file and only unlock it when you need to transfer something.
While this is a good security measure, it's not enough. Many experts recommend storing the wallet offline, either on a USB drive or an offline computer. Another good option, suggested by Armory, is to print your private keys onto a paper wallet. Obviously, then you would need to physically store that paper in a secure location.

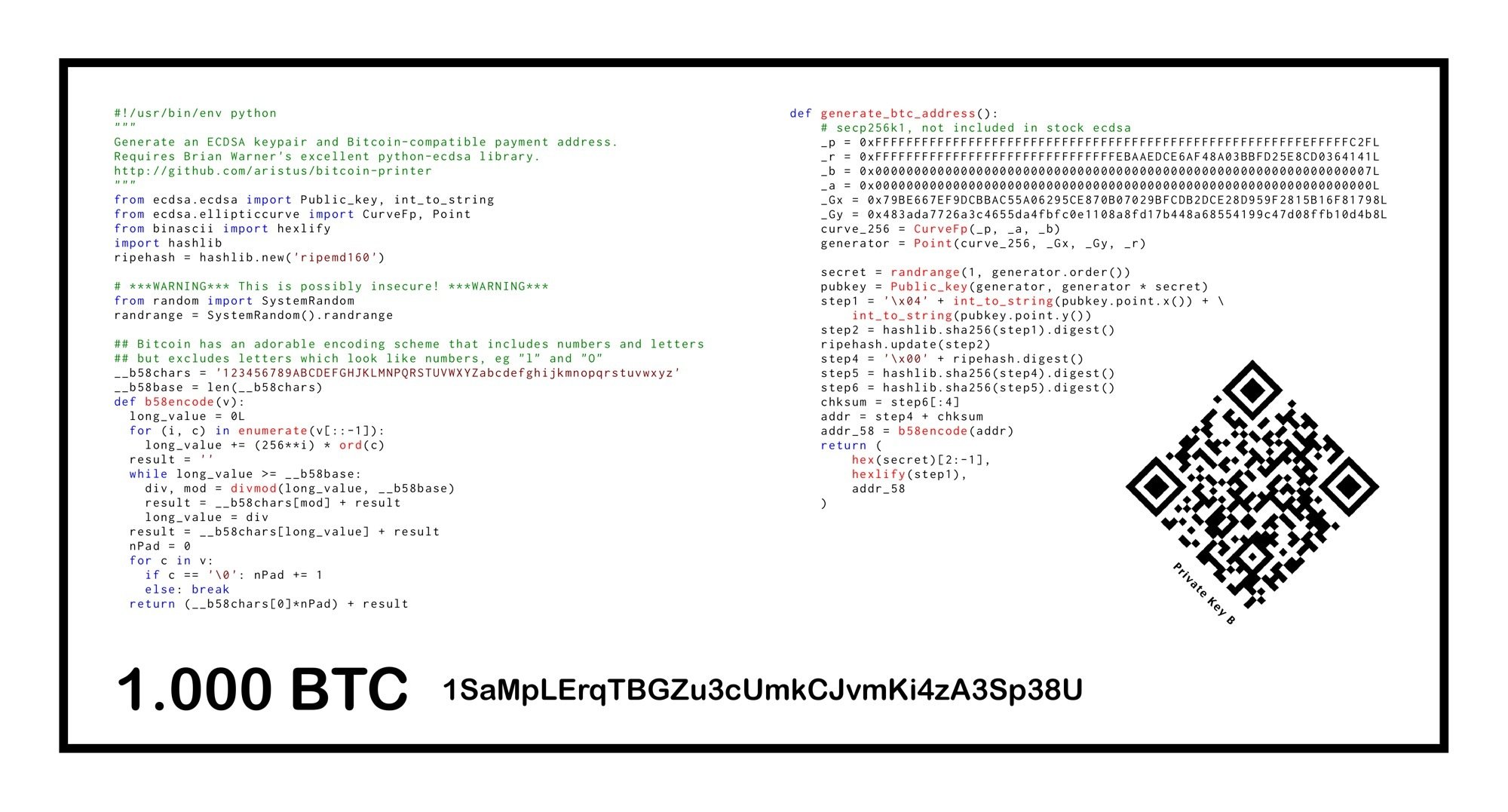
Figure 4: Bitcoin Paper wallet example (Source: Carlos Bueno)
Wallet theft protection has sparked some new ideas for security solutions. There's cold storage, or the secure storage of specific amounts of Bitcoins offline via mechanisms like 'hardware security modules', which are the same instruments financial institutions use to protect their private keys. It started as a theft countermeasure for Bitcoin exchanges, where they would move most of a customer's Bitcoins to cold storage while making a portion of them available for immediate transfer.
There are many ways to implement cold storage, one of them is using hardware wallets, a specific piece of hardware designed to be portable/secure and aimed at storing your Bitcoins. Currently, there are four hardware wallet providers – Pi Wallet, Trazor wallet, Butterfly's labs BitSafe and the more experimental Bitcoincard.

Fig. 5: Butterfly Lab's Bitcoin hardware wallet (2.0)
For customers that don't want to carry yet another real wallet, there are some companies that specialize in deep cold storage, like Seedcamp company Elliptic or Swiss-based iceVault.
Backups and deterministic wallets
Wallet backups are also problematic. When Bitcoin wallets are used for the first time, the software automatically generates a pool of new private keys for the user to use for their transactions. This pool defaults to 100 pre-generated keys. Whenever the user needs a new address, the wallet will relinquish the new private key from the pool. Though the idea isn't a bad one, it becomes problematic when it comes to backing up the wallet file since frequent backups are required for oft-used wallets.

Figure 6: Deterministic wallet vs. regular wallet example
Even worse, is the fact that wallet files weren't designed to be shared. If someone gains access to the wallet file, they'll have access to all the private keys within it. This is the reason why some of the core Bitcoin developers started working on what's called 'deterministic wallets' – a wallet that uses a seed code to derive all other public keys from it. It allows for users to backup the seed code only once and forget about outdated backup copies.
The evolution of this concept is known as hierarchical deterministic wallets (HD wallets). This enables the master private key to be fragmented into smaller keys, which control independent deterministic key chains under it in a way that allows the operation of several independent wallets that are all governed by the same secret seed code or master private key.
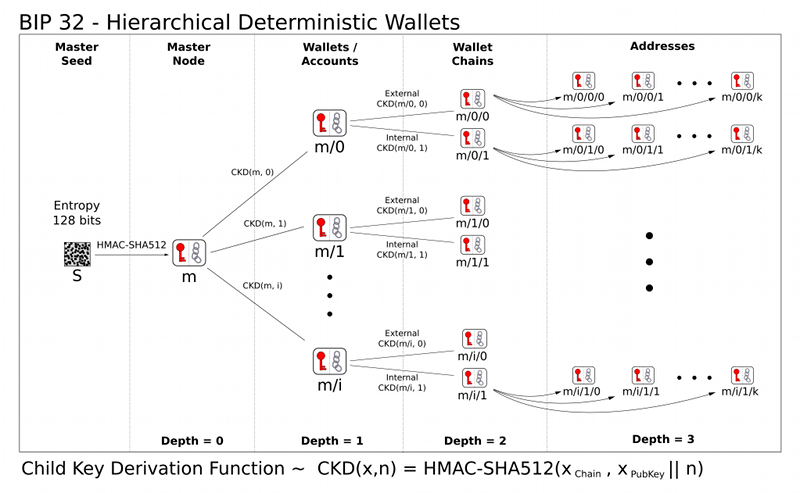
Figure 7: Hierarchical deterministic wallet
This hierarchical structure allows for the sharing of parts of the wallets with different actors, without compromising the integrity of the private keys used. There are several scenarios where this is a good thing. That said, it's also important to note that such wallet structures aren't invulnerable and also have security problems with how specific keys are shared.
There are some deterministic wallets out there like the Italian GreenWallet, but so far, there aren't many wallets that support HD wallets except Bitcoin Armory, Electrum and Coinkite. MultiBit is currently on the verge of unveiling support, too.
Anonymity detection and tumblers
One of the most appealing aspects of Bitcoin is its assumed anonymity. Is it really that anonymous, though? The truth is, as always, it lays somewhere in between. The fact that you can see all the transactions ever done in the system through the Blockchain makes fraud very difficult.
The anonymous aspect of Bitcoin is attached to the supposed randomness of the Bitcoin address, a piece of cryptographic gibberish that is automatically generated and isn't tied to any specific identity. As long as the identity of the one controlling the private key behind a Bitcoin address is hidden, anonymity could be achieved.
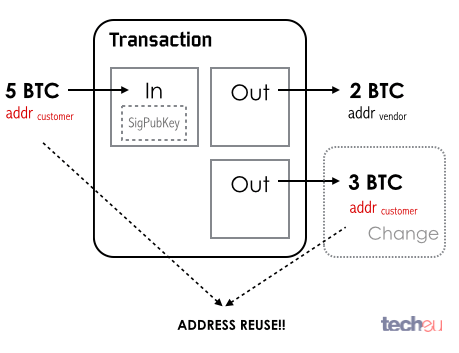
Figure 8: Bitcoin address reuse
The problem, though, is that there is always a weak link in the chain – particularly, humans. At some point, you need to disclose to someone the link between a Bitcoin address and the owner. Once an identity is latched to an address, the flow on Bitcoins can be traced through the network, making it very hard to hide the money trail. There isn't anything problematic about this, but part of Bitcoin's allure is that users don't want anyone to know how they spend their money.
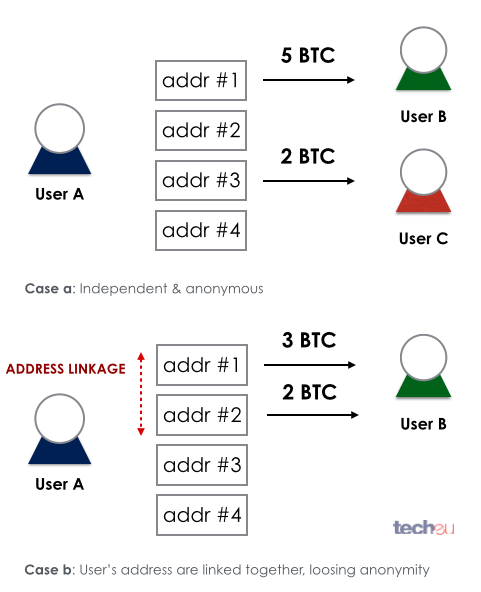
Figure 9: Bitcoin address linkage
To prevent this, the Bitcoin community suggests never reusing your Bitcoin address and making sure you keep your different Bitcoin addresses unlinked. As long as you keep them unconnected, identity exposure is minimized.
Of course, this isn't always possible, and several proposals have been drafted to hard-code better anonymous functions into the Bitcoin protocol itself, including suggestions for stealth addresses or enforcing network traffic encryption through Tor services.
One of the most obvious ways to protect privacy is using a Bitcoin tumbler service. A 'tumbler' or 'mixer' is a service that takes your Bitcoins, mixes them with other users' and returns the same amount of Bitcoins but mixed together with outputs from unrelated transactions. It is, to some degree, an exchange of Bitcoins between users in an anonymous manner so you end up getting the same amount but composed of Bitcoins from several different sources.
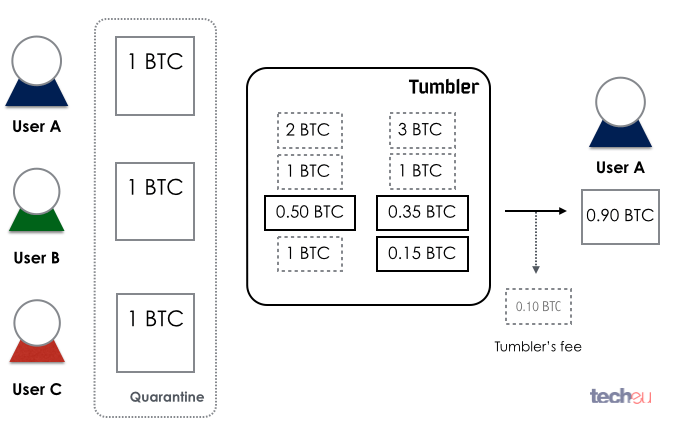
Figure 10: Bitcoin tumbler in action
Currently there are several services that will mix your Bitcoins, ranging from the secretive Bitcoinfog, to Bitmixer, Bitcoin Blender, BitcoinBath, BitSafe, CoinSplitter or Bitlaundry. There is also a big push to integrate the same principle of Bitcoin-mixing into the Bitcoin protocol – particularly, something called CoinJoin, an idea that seems to be slowly gaining use with some wallet makers, such as SharedCoin.
Last words: it's not that simple
The Bitcoin world is extraordinary, but also technologically complex.
The fact that there is money to be made and the thrill that's pulling hackers into the ecosystem creates a dangerous combination. I wouldn't be surprised to see more and more security companies devoting resources to create Bitcoin security safeguards.
That's it for now, don't forget to check back for our next post in the series. In true Bitcoin fashion, you can also donate Bitcoins here if you're liking the posts: 13kbYPnPbhPALfCpSeMgairFYj3W7etRTx.
Featured image credit: Lolostock / Shutterstock


