Today French cyber tech startup Filigran announced it had raised €5 million in seed funding. Not bad for a company that only launched in October 2022.
With over 3200 organisations using their solutions globally, the company counts public sector bodies such as the European Commission, the FBI, the New York City Cyber Command, multiple US and Australian federal agencies, the Netherlands National Police Corps, and numerous European ministries as users as well as Airbus, Marriott, Thales, Hermès, and Bouygues Telecom as customers.
It's been operational for less than a year.
I spoke to Filigran CEO and co-founder Samuel Hassine to learn more.
The company was founded by Hassine with CTO Julien Richard to fill a service gap in cybersecurity regarding cyber threat intelligence and crisis management.
Cyber threat intelligence uses data to help organisations identify emerging threats, understand attacker tactics and anticipate potential cyberattacks. Data analysed can include malicious IP addresses, domains, malware signatures, and patterns of malicious behaviour.
Filigran is developing two products for companies dealing with cyber threat intelligence, detection and incident response use cases:
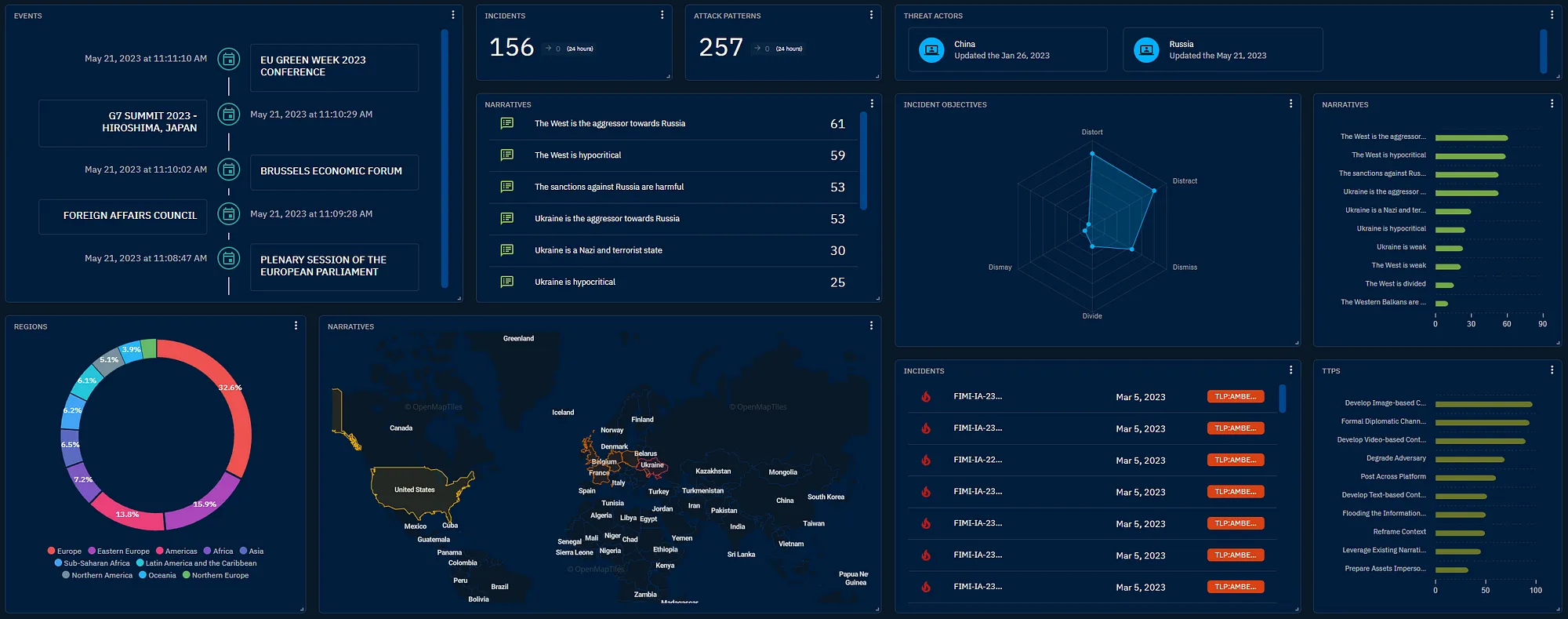
- OpenCTI - An eXtended Threat Knowledge Platform designed to help cybersecurity teams organise, store and operationalise threat intelligence information at a technical and strategic level.
- OpenEx - An eXtended Threat Simulation Platform that uses cyber threat knowledge for attack and crisis management simulations, It stress-tests the resilience of critical infrastructure (digital twins or actual infrastructure) in the face of new and emerging threats.
Hassine explained that the business evolved in response to a common industry problem. While there's a bounty of cybersecurity risk detection platforms that store and organise and manage technical data:
"There was no solution for the tactics, the campaigns, and the technical solutions that could provide a strategic plan.
For example, I'm in the retail sector and have a presence in China and France, so what are the threats that most target me? What are the indicators, and what do I need to detect them? Is it random or targeted if I receive an alert regarding an IP address or domain name?"
OpenCTI is used by hundreds of investigators and police, from the FBI to European government agencies and some of the world's largest organisations. It replaces the traditional use of wikis, excel sheets and PDF documents for strategic planning.
And the OpenEx threat simulation platform allows companies to simulate relevant, realistic scenarios as they would occur in reality:
"People work with emails and calendar invites to send a threat in a simulation exercise. OpenX brings all of this into a single platform, automating and creating scenarios with collaborative access."
For example, you can run really technical scenarios to find the weaknesses of your technical teams in terms of detections. You might find you didn't detect a threat because you don't have the appropriate tooling."
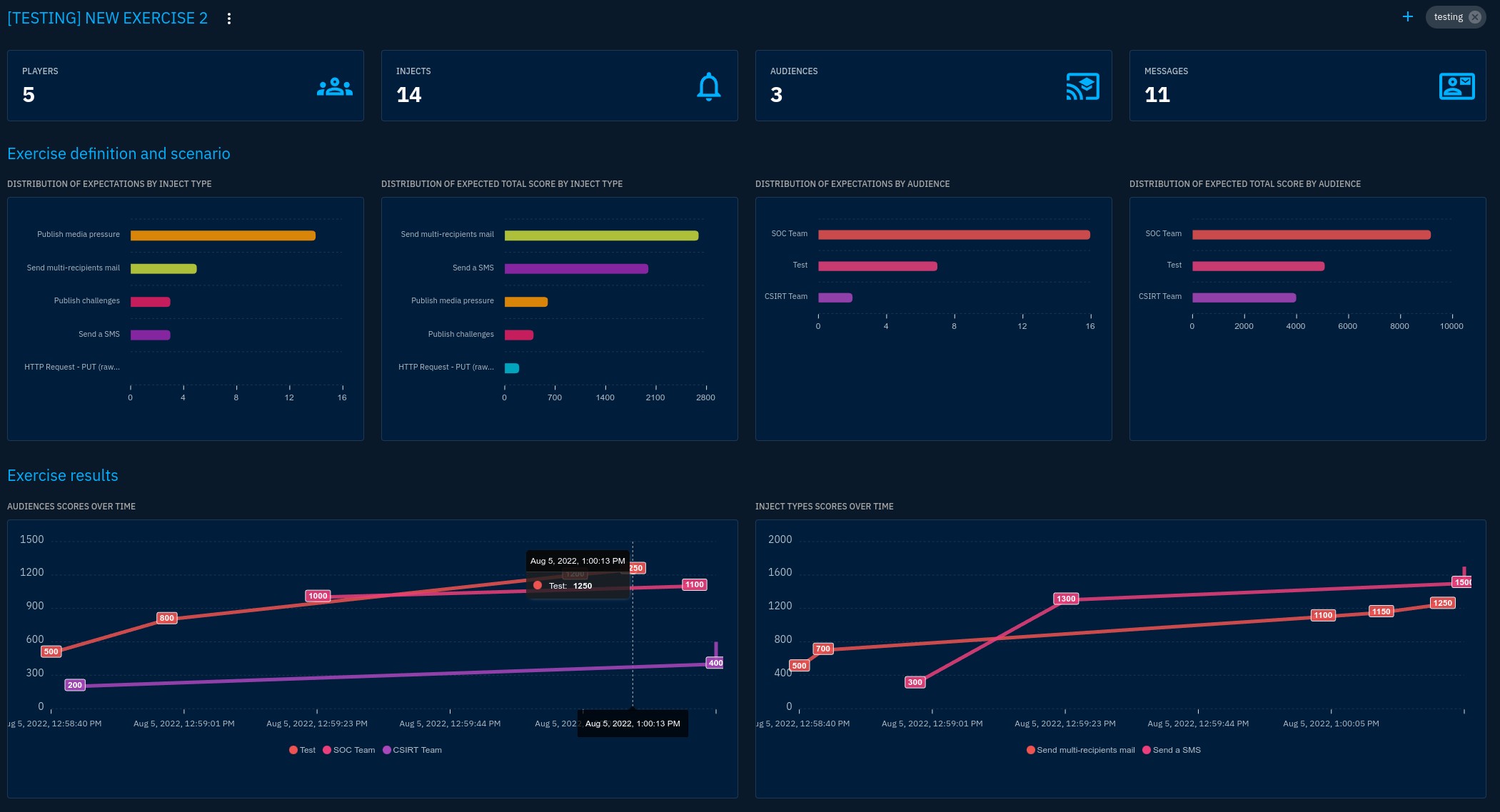
But Hassan explains that in most cases, the problem was not that they didn't see the threat; the problem was that they saw it in the middle of hundreds of alerts without the context to know whether an act occurred as the result of an administrative error or test or was really malicious.
This is where the OpenCTI platform steps in, providing a means to assess any anomalies' risk level.
Further, the reality of a cyberattack such as a ransomware attack is that things move fast.
"There's a procedural challenge of what needs to happen and by whom, but also dealing with a plethora of different stakeholders, from those asking for the ransom to senior management and board members because the incident is leaking on Twitter."
Hassine detailed:
"At some point, they don't know what to do. 'Do we have to pay the ransom or not? I called my insurance. They said, maybe yes, but this other organisation is saying no, don't pay.' So it's mostly a problem of tough standard operating procedures and training. This is why training is really important."
The challenge of moving fast and growing big at speed
With a rapidly expanding user base, the company had a problem not uncommon to startups – their product was two guys in a garage developing it in their spare time.
So while rapidily onboarding new staff, the security community found something that worked and shared Filigram's platforms among their networks:
"It was fast, virtual adoption. One guy started using the platform at the Marriott; he moved to HashiCorp to head up the lead of the threat intelligence team there and brought the platform with him. Someone came from a French startup in cybersecurity to the Netherlands police and introduced the platform."
This first round of funding was led by UK investor Moonfire with additional investments from Motier Ventures, Kima Ventures, Raise Sherpas, Zebox Ventures and others.
The investment will fund an 18-month business acceleration plan focused on engineering, customer success and commercial growth in Europe and North America, as well as support and consulting for customers who use Filigran's eXtended Threat Management on-premises; and development of Filigran's subscription-based multi-cloud SaaS offering.



Would you like to write the first comment?
Login to post comments